Security
Transferring sensitive PME configuration information between systems and IT networks introduces security risks.
 warning
warning
potential compromise of System availability, integrity, and confidentiality
Use cybersecurity best practices to help prevent unauthorized access to the software.
Failure to follow these instructions can result in death, serious injury, equipment damage, or permanent loss of data.
Work with facility IT System Administrators to ensure that the system adheres to the site-specific cybersecurity policies.
Carefully review the following information to understand the potential security risks that are introduced when you use the Configuration Manager, and how to minimize these risks.
NOTE: The information contained in this topic is not exhaustive; if you are uncertain about security protocols, consult your IT department.
Managing the PME system key
(The following applies to PME version 8.2 and newer)
In order to write a source system archive to a PME target system, a copy of the source system key is required. During the write to system work flow, you are prompted to enter the source system key:
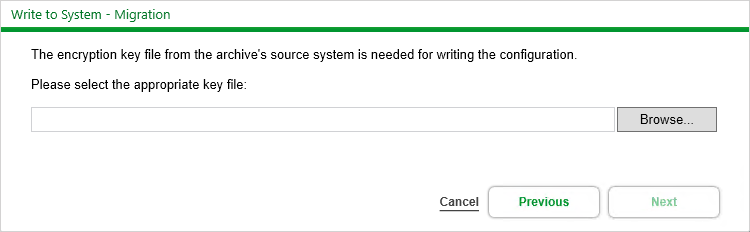
The source system key can be exported from the source system using the PME installer.
NOTE: Keep the system key in a secure location, protected from unauthorized access.
The Configuration Manager displays a reminder for the need to export the key at the end of a save to archive for a PME configuration:
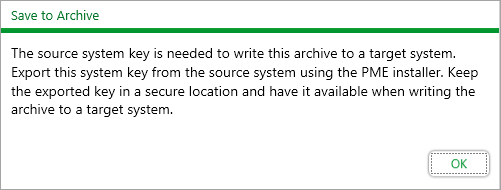
NOTE: No system key is required for writing PME 7.2.2 archives.
NOTE: The Configuration Manager cannot determine if the provided key is correct for the source system configuration. If an incorrect key is provided, the write to system will continue without warnings. However, the following Reconfigure step in the migration process will fail and the target system will not be functional. To correct the situation see Reconfigure fails after Write to System.
Attaching files to an archive
The following table lists the potential security risks that could arise when you attach files to an archive:
| Configuration Manager Behavior | Security Risk |
|---|---|
| Files can be added to a configuration as attachments. | An attached file could introduce malicious software or viruses into a configuration archive. |
| Configuration Manager runs in an Administrator level Windows account. | Malicious software or viruses would have the same level of access to the server. |
| Configuration Manager uses PME supervisor-level account access. | Malicious software or viruses would have the same level of access to PME. |
| PME is typically installed on a server type computer in a customer network. | Malicious software or viruses loaded into PME might infect the entire network. |
To minimize the risk of someone using the Configuration Manager to introduce malicious software or viruses into a PME system or an IT network:
- Virus scan all files before attaching them to a configuration.
- Be certain that you know where an archived configuration comes from before you write it to a system.
- Virus scan all attached files that are written to the target machine.
- Follow all corporate security policies.
Adding a password when saving an archive
An archive contains detailed and sensitive information about a PME system. Unauthorized individuals might gain access to this information.
Given this security risk, consider using the following safety precautions when working with the Configuration Manager:
- Add a password when you save a configuration to an archive
- Do not share a saved configuration archive
- Follow all corporate security policies.
When you save a configuration to an archive, you are prompted to enter a password:
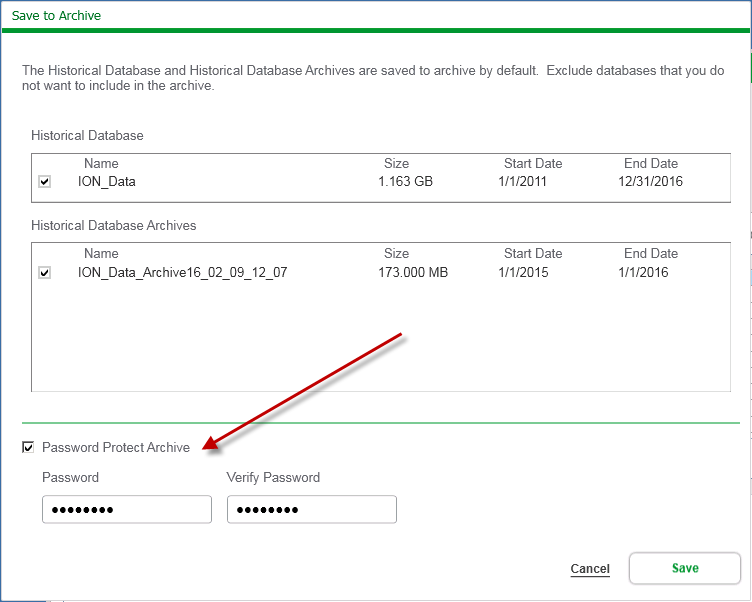
A password-protected archive cannot be loaded into Configuration Manager without providing the correct password. Additionally, files in a password-protected archive cannot be opened or copied without providing the password: