Tunneling of OPC data
The networking protocol for OPC is DCOM. DCOM is difficult to configure, responds poorly to network interruptions, produces high network traffic, and has significant security weaknesses.
OPC tunneling applications are designed to overcome these limitations when using OPC over a network. The goal of OPC tunneling is to eliminate DCOM by replacing it with a network protocol like TCP. Instead of connecting the OPC client to a networked OPC server, the client program connects to a local OPC tunneling application, which acts as a local OPC server. The tunneling application accepts requests from the OPC client and converts them to TCP messages, which are then sent across the network to a companion tunneling application on the OPC server computer. There the request is converted back to OPC and is sent to the OPC server application for processing. Any response from the server is sent back across the tunnel to the OPC client application in the same manner.
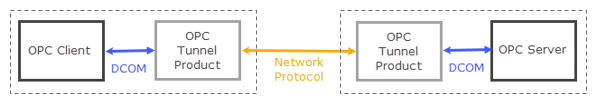
Diagram: OPC data is sent over the network by OPC tunneler using common network protocols.
OPC tunneling products are available from several vendors, including Kepware and Matrikon.
When selecting OPC tunneling applications, look for products that
- keep the synchronous OPC transactions local to the client and server, with an asynchronous tunnel connection
- provide link monitoring
- handle network disruptions effectively
- meet your security needs