Managing certificates
By default, Power Operation is installed so that web services and web applications are set up to use the Transport Layer Security (TLS) 1.3 encryption protocol with self-signed certificates.
- To manually set up certificates, use the following procedures:
- In a redundant system, you must replicate certificates from one server to the other. Use the following procedure:
- To configure third-party certificates for use with Power Operation, refer to the following topic:
Configuring browser encryption
- Navigate to Administrative Tools and open Internet Information Services (IIS).
- In the left Connections pane, select [Machine Name] > Sites > Default Web Site.
- In the right Actions pane, select Bindings.
- In the Site Bindings window, select https and select Edit.
- In the Edit Site Binding window, in the SSL certificate drop-down, select [Machine Name] Grpc Certificate.
- Select OK to close the Edit Site Binding window, then select Close to close the Site Bindings window.
- Restart IIS.
To apply a third-party certificate, see Configuring third-party certificates.
Configuring without encryption (not recommended)
Setup browser configuration to work in Google Chrome.
- Type chrome://flags in the URL area of Google Chrome.
-
Search for Insecure origins treated as secure and enter the IP address.
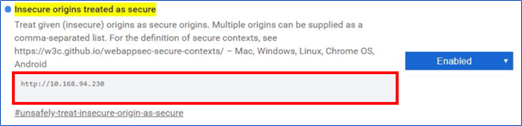
NOTE: Use the Power Operation web server IP address.
- Set Insecure origins treated as secure to Enabled.
NOTE: You will not receive the pop-up message if Enabled is not selected for this setting.
Replicating self-signed certificates from one server to the other in a redundant system
In a redundant system, you must replicate certificates from one server to the other.
To use the installed, self-signed certificates in a redundant system:
- Open the Application Configuration Utility and navigate to the Certificate Management > Redundancy Management tab. Do the following:
- On the Redundancy Management page, follow the instructions to export certificates from the primary machine to a secondary system.
- On the Redundancy Management page, follow the instructions to import the certificate to the secondary system.
- Use the Information tab to compare the Root Certificate Thumbprint and the Certificate Thumbprint. The values must be identical.
- Using Task Manager, cycle CoreServiceHost:
- Right-click, select Stop, then right-click and select Start. Do not use Restart.
- Open Windows Command Prompt and type
iisreset, and then press Enter to restart Internet Information Services (IIS). - Navigate to ..\Program Files (x86)\Schneider Electric\Power Operation\v [version #]\Applications\Services\Platform Server\Logs.
- Open the Platform Server logs and verify that the connection is being made to both Platform Servers. A successful connection is displayed in the following example:
"[2022-04-04 10:35:23.570 AM [Information] Connected to web service at SECONDARY:23200
[2022-04-04 10:35:23.571 AM [Information] Connected to web service at PRIMARY:23200"To configure third-party certificates for use with Power Operation, see Configuring third-party certificates.
Troubleshooting
If the Platform Server Log includes or shows the error message: "Unable to connect to the web service PRIMARY:23200", you may need to add environmental variables to ignore proxy settings.
To add environmental variables:
- Open System Properties, and navigate to Advanced > Environment Variables.
- In the Environment Variables dialog, in the System variables section, create a NO_PROXY variable.
- Select OK.
- Restart the services again and check the logs, as described in step 4 and 5 previous.
For more information on platform and service layer ports, see Default port numbers.