Monitoring the Event Log
Event logs can assist with monitoring suspicious activity and identifying the cause of cybersecurity breaches that could lead to a cybersecurity incident. The Security Viewer lets you view user activity within your system. This screen lists all user actions that are captured in the Event Log.
By default, event logs are not shared with unauthorized users. Events are read only and cannot be changed.
Viewing event logs in the Security Viewer
-
In the Power Operation Runtime, select the Alarms/Events tab, and then select Security Viewer.
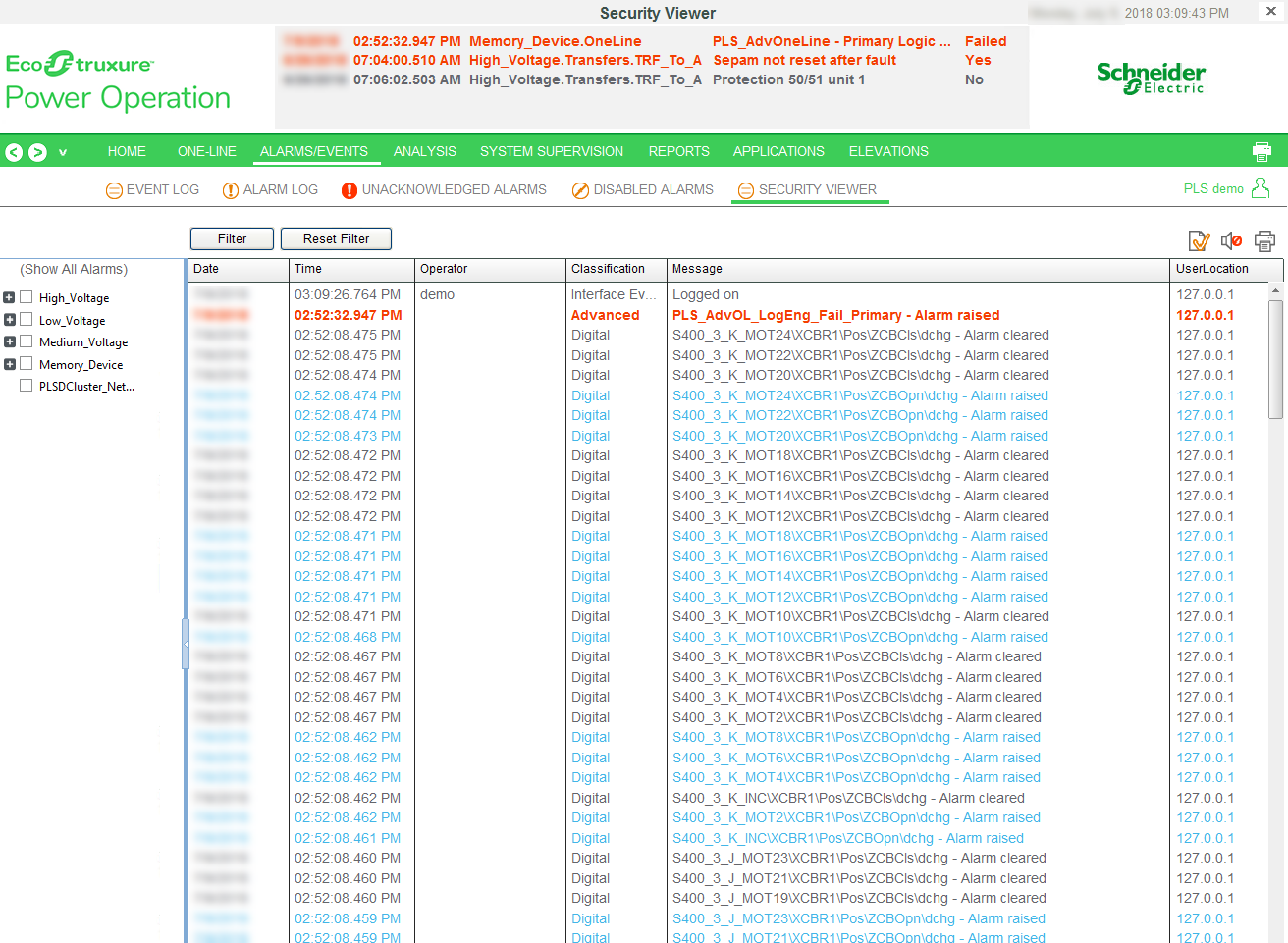
The screen displays a table with the following default columns:
|
Date |
The date that the activity was logged. |
|
Operator |
User name from the Citect users. |
|
Time |
The time that the activity was logged. |
|
Classification |
The class of the event. |
|
Message |
From the Message field in the Alarm Log. |
|
UserLocation |
URL of the computer at which the activity occurred. |
For more information on these fields, see Alarm SOE fields in the Plant SCADA help. Go to the AVEVA Knowledge & Support Center website for information on Plant SCADA.
To change the view of the log, you can use any of the sort or filter features that are available in the Event Log.
Filtering information:
- To the left of the log, check one or more of the devices in the system. This filters information to include data only for those devices. When nothing is checked, all devices are included.
- You can insert and remove columns.
-
Right-click in the header area of the log, then choose Insert Column. From the list that appears, check an additional column title. The new column displays to the left of the column you clicked.
-
Right-click on the header of the column you want to delete and then select Remove Column.
- You can filter that data that is included. To do this, use the Security Viewer filter. For instructions on filtering the columns in the log, see Using the Security Viewer Filter.
To add a column:
To remove a column: