The EmailHandling library provides email client functions that allow your controller to send emails to one or several recipients with the possibility to customize the content. The protocol type used is SMTP as standard for email traffic. It is also possible to receive or delete emails from a server using the Post Office Protocol 3 (POP3).
This library supports SMTP and POP3 via a secured connection using TLS.
Whether a connection using TLS is supported depends on the controller where the FB_TcpClient2 is used. Refer to the specific manual of your controller to verify if TCP communication using TLS is supported.
You can connect your controller to an email server to send emails that inform about your machine status or report on key performance indicators.
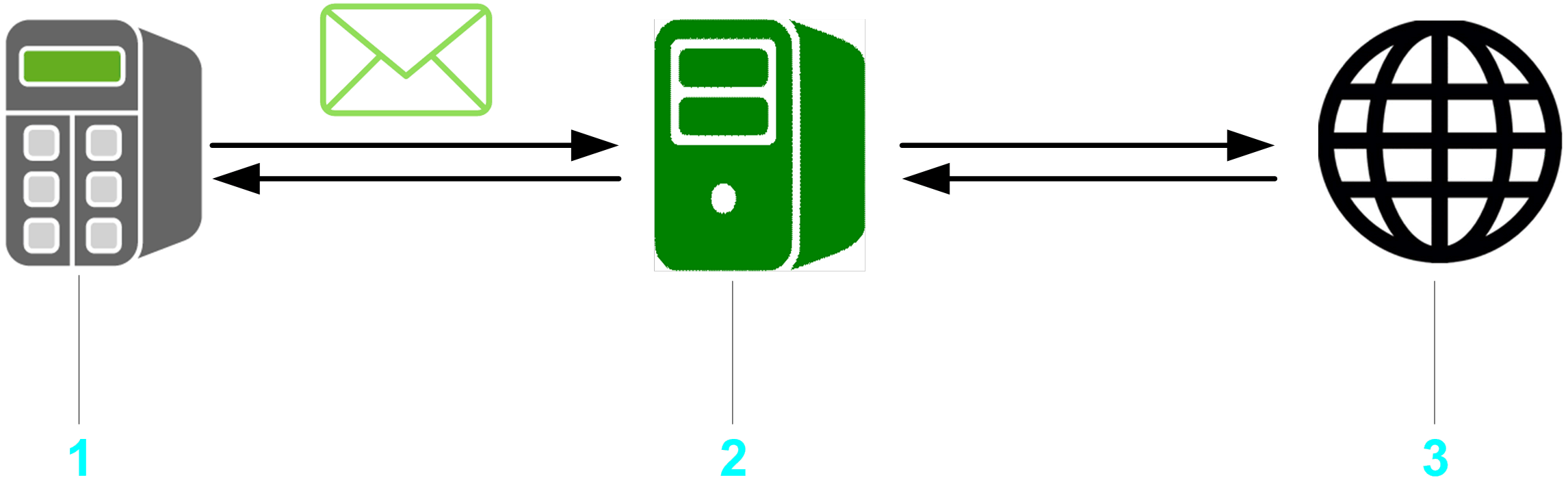
1 Controller
2 Email server
3 Recipients/Sender
Characteristics of the Library
The following table indicates the characteristics of the library:
|
Characteristic |
Value |
|---|---|
|
Library title |
EmailHandling |
|
Company |
Schneider Electric |
|
Category |
Communication |
|
Component |
Internet Protocol Suite |
|
Default namespace |
SE_EMail |
|
Language model attribute |
|
|
Forward compatible library |
Yes (FCL) |
NOTE: For this library, qualified-access-only is set. This means, that the POUs, data structures, enumerations, and constants have to be accessed using the namespace of the library. The default namespace of the library is SE_EMail.
In conjunction with the library, the example project EMailHandlingExample.project is provided. The example project shows how to implement the components from the EmailHandling library.
|
Step |
Action |
Comment |
|---|---|---|
|
1 |
In the EcoStruxure Machine Expert Logic Builder, execute the command New Project. |
– |
|
2 |
In the New Project dialog box, select From Example from the Project type list. |
– |
|
3 |
On the right-hand side of the New Project dialog box, select the controller (1) from the Controller list. |
Result: Available examples are listed in the Matching Examples text box. |
|
4 |
Select your example from the Matching Examples list. |
– |
|
5 |
Enter a name for the new project, and select the file location. |
– |
|
6 |
Click the OK button. |
Result: A new project is created based on the selected example. |
(1) PacDrive LMC Pro/Pro2, TM251MESE, TM262M25MESS8T
Consider the following limitations for email transfer:
oOnly ASCII symbols are supported.
oOnly IPv4 IP addresses are supported.
oThe EmailHandling incorporates pointers on addresses.
oReceive acknowledgement is not supported.
oSending or receiving files via email leads to loss of file attributes.
oIn case the address of a recipient does not exist, it depends on the configuration of the server whether a feedback mail is created or whether the FB_SendEMail is able to create a diagnostic message.
oArchiving emails (sent and received items) has to be performed in the application program. Automatic storage of email traffic on the controller file system is not implemented because emails are mainly handled in the controller RAM (Random Access Memory).
Executing the Online Change command can change the contents of addresses.
|
|
|
INVALID POINTER |
|
Verify the validity of the pointers when using pointers on addresses and executing the Online Change command. |
|
Failure to follow these instructions can result in injury or equipment damage. |
The library described in this document internally uses the TcpUdpCommunication library.
The TcpUdpCommunication (Schneider Electric) and the CAA Net Base Services library (CAA Technical Workgroup) use the same system resources on the controller. The simultaneous use of both libraries in the same application may lead to disturbances during the operation of the controller.
|
|
|
UNINTENDED EQUIPMENT OPERATION |
|
Do not use the library TcpUdpCommunication (Schneider Electric) together with the library CAA Net Base Services (CAA Technical Workgroup) simultaneously in the same application. |
|
Failure to follow these instructions can result in death, serious injury, or equipment damage. |
NOTE: Schneider Electric adheres to industry best practices in the development and implementation of control systems. This includes a "Defense-in-Depth" approach to secure an Industrial Control System. This approach places the controllers behind one or more firewalls to restrict access to authorized personnel and protocols only.
|
|
|
UNAUTHENTICATED ACCESS AND SUBSEQUENT UNAUTHORIZED MACHINE OPERATION |
|
oEvaluate whether your environment or your machines are connected to your critical infrastructure and, if so, take appropriate steps in terms of prevention, based on Defense-in-Depth, before connecting the automation system to any network. oLimit the number of devices connected to a network to the minimum necessary. oIsolate your industrial network from other networks inside your company. oProtect any network against unintended access by using firewalls, VPN, or other, proven security measures. oMonitor activities within your systems. oPrevent subject devices from direct access or direct link by unauthorized parties or unauthenticated actions. oPrepare a recovery plan including backup of your system and process information. |
|
Failure to follow these instructions can result in death, serious injury, or equipment damage. |
By configuring a white list with the input i_pbyWhiteListSender, the entries of this list will be compared to the sender email specified in the header of the received email. This feature does not provide any protection against intentional manipulation of the header field From: inside the received email.
No antivirus program is available on the controller. Consider configuring one on server side.