General Information
Library Overview
The FastSampling library provides objects for sampling data from Schneider Electric drive parameters with a higher resolution than provided by the Sercos cycle.
The figure illustrates the general data sampling process:
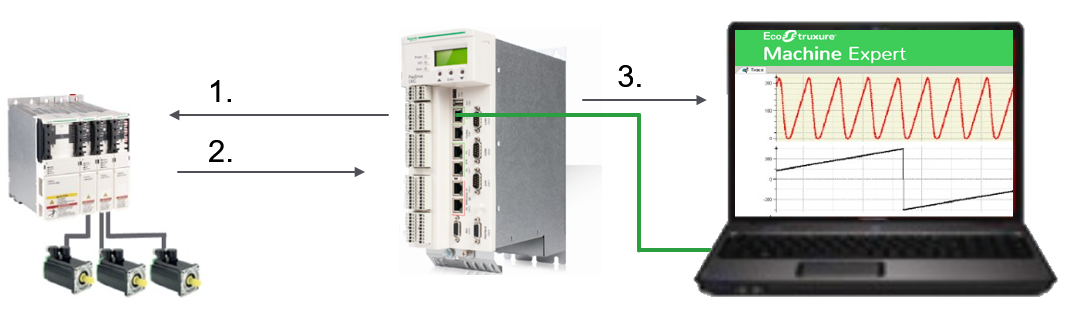
| Process step | Description |
| 1 | Fast sampling parameters are configured in the controller and the sampling process is started. |
| 2 | Configured parameter data is retrieved from the drive. |
| 3 | The controller is stopping the sampling process, saves the sampled data to an ARRAY and provides them to EcoStruxure Machine Expert. They can be displayed in a individual IEC trace graph dedicated to fast sampling results. |
Data Sampling Methods
According to the performance provided by your system, retrieving sampled data from the drive can be performed in two different ways. A specific function block is provided for each sampling method:
|
Data Sampling Method |
Function Block |
Description |
|---|---|---|
|
Asynchronous |
For systems providing restricted performance. Sampled data is buffered in the drive. |
|
|
Real-time |
For high-performance systems. Sampled data is transferred in a continuous stream by the Sercos real-time channel. |
Characteristics of the Library
The table indicates the characteristics of the library:
|
Characteristic |
Value |
|---|---|
|
Library title |
FastSampling |
|
Company |
Schneider Electric |
|
Category |
|
|
Component |
PacDrive |
|
Default namespace |
|
|
Language model attribute |
|
|
Forward compatible library |
Yes FCL |
Controller and Drive Platforms
The FastSampling library is supported by the following platforms:
-
PacDrive LMC Eco and PacDrive LMC Pro/Pro2 motion controllers
-
Lexium 62 Advanced and Lexium 62 Standard drives
with hardware revision RS10 and higher
General Considerations
| WARNING | |
|---|---|
For more information on organizational measures and rules covering access to infrastructures, refer to ISO/IEC 27000 series, Common Criteria for Information Technology Security Evaluation, ISO/IEC 15408, IEC 62351, ISA/IEC 62443, NIST Cybersecurity Framework, Information Security Forum - Standard of Good Practice for Information Security.