The library SqlRemoteAccess provides SQL (Structured Query Language) client function blocks that allow your controller to connect to an SQL database in order to run SQL queries for reading and writing data.
The communication between the controller that acts as an SQL client and the SQL database server is running via the Schneider Electric SQL Gateway. Therefore, you have to install the SQL Gateway that is supplied with EcoStruxure Machine Expert as an optional component and that requires a specific license before you can use the SQL function. For further information, refer to the SQL Gateway User Guide.
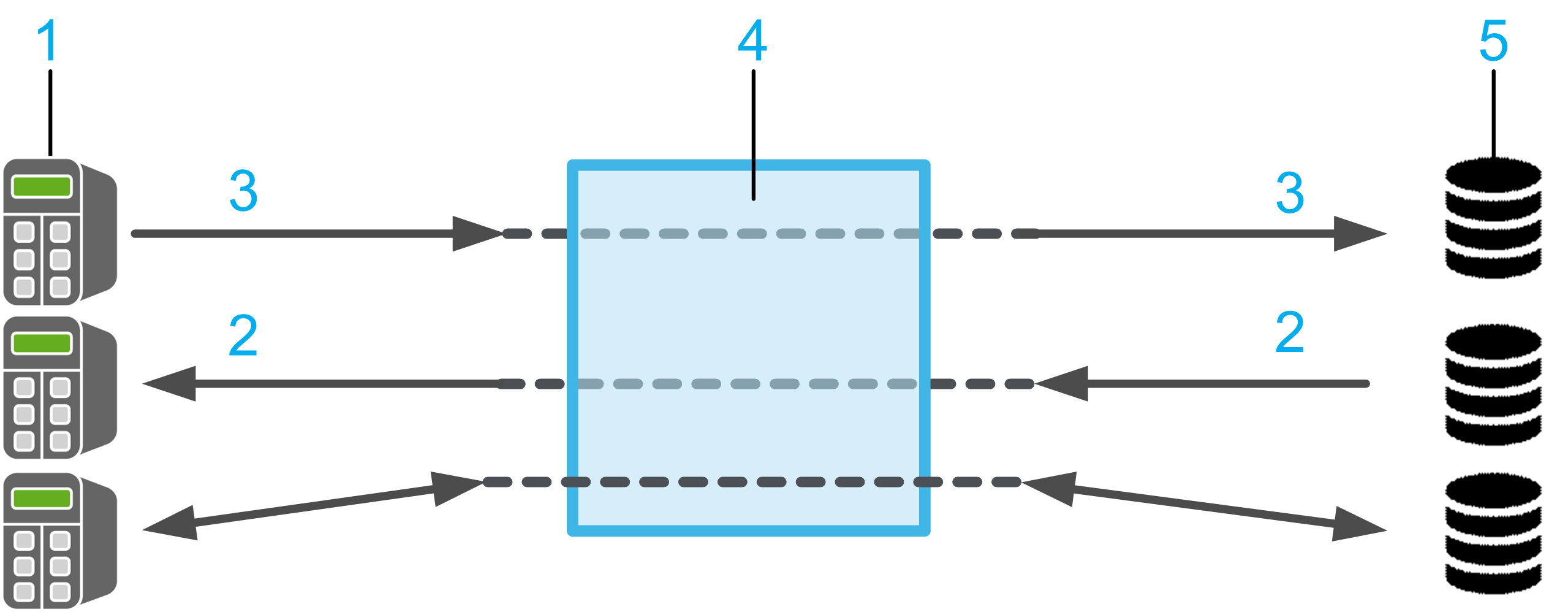
1 1...n controllers (SQL clients)
2 Read data
3 Write data
4 SQL Gateway
5 1...n database servers
After successful installation, the controller can send a customized SQL query to the database server, for example:
oQuerying data from tables.
oInserting, changing, and deleting data in tables.
oExecuting database procedures.
Characteristics of the Library
The following table indicates the characteristics of the library:
|
Characteristic |
Value |
|---|---|
|
Library title |
SqlRemoteAccess |
|
Company |
Schneider Electric |
|
Category |
Communication |
|
Component |
SQL Library |
|
Default namespace |
SE_SQL |
|
Language model attribute |
|
|
Forward compatible library |
Yes (FCL) |
NOTE: For this library, qualified-access-only is set. This means, that the POUs, data structures, enumerations, and constants have to be accessed using the namespace of the library. The default namespace of the library is SE_SQL.
In conjunction with the library, the example project SQLRemoteAccessExample.project is provided. The example project shows how to implement the components from the SqlRemoteAccess library.
|
Step |
Action |
Comment |
|---|---|---|
|
1 |
In the EcoStruxure Machine Expert Logic Builder, execute the command New Project. |
– |
|
2 |
In the New Project dialog box, select From Example from the Project type list. |
– |
|
3 |
On the right-hand side of the New Project dialog box, select All from the Controller list. |
Result: Available examples are listed in the Matching Examples text box. |
|
4 |
Select your example from the Matching Examples list. |
– |
|
5 |
Enter a name for the new project, and select the file location. |
– |
|
6 |
Click the OK button. |
Result: A new project is created based on the selected example. |
Consider the following limitations for SQL communications:
oOnly IPv4 (Internet Protocol version 4) is supported.
oOnly database data types supported which conform to IEC 61131-3.
oRead and write BLOB (Binary Large Objects) objects from and into a database is not supported.
The library described in this document internally uses the TcpUdpCommunication library.
The TcpUdpCommunication (Schneider Electric) and the CAA Net Base Services library (CAA Technical Workgroup) use the same system resources on the controller. The simultaneous use of both libraries in the same application may lead to disturbances during the operation of the controller.
|
|
|
UNINTENDED EQUIPMENT OPERATION |
|
Do not use the library TcpUdpCommunication (Schneider Electric) together with the library CAA Net Base Services (CAA Technical Workgroup) simultaneously in the same application. |
|
Failure to follow these instructions can result in death, serious injury, or equipment damage. |
Considerations Concerning Cyber Security
The SqlRemoteAccess library functions do not support secure connections such as TLS (Transport Layer Security) or SSL (Secure Socket Layer) to the SQL Gateway. Communication must only be performed inside your industrial network, isolated from other networks inside your company, and protected from the Internet.
NOTE: Schneider Electric adheres to industry best practices in the development and implementation of control systems. This includes a "Defense-in-Depth" approach to secure an Industrial Control System. This approach places the controllers behind one or more firewalls to restrict access to authorized personnel and protocols only.
|
|
|
UNAUTHENTICATED ACCESS AND SUBSEQUENT UNAUTHORIZED MACHINE OPERATION |
|
oEvaluate whether your environment or your machines are connected to your critical infrastructure and, if so, take appropriate steps in terms of prevention, based on Defense-in-Depth, before connecting the automation system to any network. oLimit the number of devices connected to a network to the minimum necessary. oIsolate your industrial network from other networks inside your company. oProtect any network against unintended access by using firewalls, VPN, or other, proven security measures. oMonitor activities within your systems. oPrevent subject devices from direct access or direct link by unauthorized parties or unauthenticated actions. oPrepare a recovery plan including backup of your system and process information. |
|
Failure to follow these instructions can result in death, serious injury, or equipment damage. |
|
Function block / function |
Use |
|---|---|
|
Performs SQL requests that read data from the SQL database. |
|
|
Performs SQL requests that update or modify the SQL database. |
|
|
Converts an enumeration element of type ET_Result to a string variable. |
Overview of the Structures in the Module-Specific Interface
|
Structure |
Use |
|---|---|
|
Contains the information for connecting to an SQL Gateway and information on the SQL database. |
|
Enumeration |
Use |
|---|---|
|
Contains the possible values that indicate the result of operations executed by the function block. |